Schwäbisch-Hall setzt mit UCS auf eine nachhaltige IT-Infrastruktur
Im Januar 2021 hatte ich im Rahmen einer Stellenausschreibung über die Linux-basierte IT der Stadt Schwäbisch Hall berichtet und in diesem Zusammenhang ein Interview mit Mathias Waack, dem Leiter des Fachbereichs Organisation und IT geführt. Er verwaltet für die IT der Stadt über 600 Linux-Clients samt dazugehöriger Server.
https://linuxnews.de/schwaebisch-hall-setzt-mit-ucs-auf-eine-nachhaltige-it-infrastruktur/

Schwäbisch-Hall setzt mit UCS auf eine nachhaltige IT-Infrastruktur
Schwäbisch Hall setzt seit 20 Jahren auf Linux in der Verwaltung. Kürzlich wurde eine Migration auf den Univention Corporate Server erfolgreich abgeschlossen.LinuxNews
btrbk is awesome
https://ounapuu.ee/posts/2022/07/09/btrbk-is-awesome/
fex - flexible token-field extraction
Sometimes simpler than cut and awk
cut(1) from GNU coreutils (on Linux) does not support negative offsets, so you cannot ask cut to only show you the Nth field from the end. Additionally, to cut by multiple fields, you end up having to write cut ... | cut ... | cut ...
awk lets you select negative offsets using the NF variable. Get the 2nd to last field with $(NF - 1). However, cutting multiple times still requires multiple awk invocations or using awk’s split() function multiple times.
https://www.semicomplete.com/projects/fex/
fex - flexible token-field extraction - semicomplete
What is fex? Fex is a powerful field extraction tool. Fex provides a very concise language for tokenizeing strings and extracting fields. The basic usage model is that you provide a series of delimiter and field selection pairs.semicomplete
benedict16b mag das.
Die unabhängige Distribution Void Linux im Test
Viele Linux-Distributionen basieren auf etablierten Varianten des freien Betriebssystems und übernehmen damit bewährte Technologien. Doch zunehmend tauchen auch unabhängig aus den Quellen entwickelte neue Linux-Derivate auf, die sich vor allem an Anwender mit älterer Hardware richten und den Fokus auf ein schlankes System legen. Das aus Spanien stammende und noch sehr junge Void Linux [1], soeben erst in der zweiten Version erschienen, sieht sich dagegen als Allrounder für unterschiedlichste Hardware-Plattformen. Neben einem ressourcenschonenden Design zeichnet sich “The Void” vor allem durch eine Vielzahl neu entwickelter Kernkomponenten aus, die auch vor dem Paketmanagement und sogar dem Init-System nicht halt machen.
https://www.linux-community.de/ausgaben/linuxuser/2016/04/alles-neu2/

Die unabhängige Distribution Void Linux im Test - LinuxCommunity
Viele abgespeckte Distributionen für betagte Computer wollen primär Einsteiger ansprechen. Wollen Sie dagegen auch auf alten Einkern-Prozessoren neue Technologien einsetzen, und schrecken Sie vor der Kommandozeile nicht zurück, dann sollten Sie sich …Computec Media GmbH
A Tutorial for Isolating Your System with Linux Namespaces
Linux namespaces make it possible to run a whole range of applications on a single real machine and ensure no two of them can interfere with each other, without having to resort to using virtual machines. In a single-user computer, a single system environment may be fine. But on a server, where you may want to run multiple services, it is essential to security and stability that the services are as isolated from each other as possible.
https://www.toptal.com/linux/separation-anxiety-isolating-your-system-with-linux-namespaces

Separation Anxiety: A Tutorial for Isolating Your System with Linux Namespaces
Toptal engineer Mahmud Ridwan dives into the Linux kernel with this in-depth guide to Linux namespaces, and how you can use them to create robust isolated environments on your Linux machine.Mahmud Ridwan (Toptal)
PGP Encryption: How It Works and How You Can Get Started
Don’t let the name “Pretty Good Privacy” mislead you. PGP encryption is the gold standard for encrypted communication and has been used by everyone from nuclear activists to criminals since its invention in 1991. While the execution is complex, the concept is simple: you can encrypt text, making it unreadable to anyone who doesn’t have the key to decode it.
https://www.maketecheasier.com/pgp-encryption-how-it-works/

PGP Encryption: How It Works and How You Can Get Started - Make Tech Easier
Heard of PGP encryption, but have no idea what it means? Find out how it works and how you can encrypt files using PGP.Crystal Crowder (Make Tech Easier)
8 Simple Ways to Securely Delete Files in Linux
We have seen how to fully erase the contents of your hard disk, but what happens if all you want is to permanently delete one, two or a dozen files? This guide shows you some of the most popular solutions for complete file deletion in Linux.
https://www.maketecheasier.com/completely-delete-file-in-linux/

8 Simple Ways to Securely Delete Files in Linux - Make Tech Easier
Secure deletion does not always mean wiping an entire hard disk. Learn how you can securely delete your individual files in Linux.Ramces Red (Make Tech Easier)
Vanilla OS is an Immutable Linux-based distribution which aims to provide a vanilla GNOME experience.
Nicely Updated.
Designed to last over time and always be faithful to you.
Vanilla OS is an immutable and atomic Ubuntu Linux-based Point Release distribution, that receives updates at the right time, neither before nor after, without sacrificing security and functionality.
Immutable..
..but also not.
Vanilla OS is an immutable operating system, core parts of the system are locked down to prevent unwanted changes and corruption from third-party applications or a faulty update. Some paths are still writable, such as the home and configurations directories, this allows the user to keep their files and ensure the normal functioning of applications.
Core components are only updated via controlled and atomic transactions, which are applied only on success and made available on reboot.
Vanilla OS uses an A/B structure (ABRoot), which transacts updates atomically between two root micro partitions. The benefits of this system are the guarantee that the system is altered only when the entire transaction is successful (concept of atomicity), furthermore, the double root partition structure allows you to roll back to the previous state, directly from your boot, you will always have a home to come back to.
This structure, unlike others, is compatible with already existing distributions and does not require a complex setup and allows easy re-initialization of the system without data loss.
Tuxsucht.de - Linuxsuchmaschine
Was macht Tuxsucht.de?
Tuxsucht sucht für dich nach Linux und zwar nur nach Linux. Egal nach was du suchst, Tuxsucht durchsucht für dich alle großen deutschsprachigen Linuxforen, renomierte Blogs und auch viele auf Linux-taugliche Hard- und Software spezialisierte Shops. So kommst du schneller an die von dir benötigten Informationen.
Warum sollte man Tuxsucht.de benutzen?
Thomas sucht nach einer neuen Webcam, doch Informationen - ob diese Webcam unter Linux gut funktioniert - zu finden erweist sich als schwierig. Die obersten Treffer einer Websuche sind durch Suchmaschinenspam belegt, die nächsten Treffer sind nur in Englisch. So kommt bei Thomas schnell Frust auf. Tuxsucht erleichtert Thomas seine Suche, da nur in einer Auswahl aller großen deutschsprachen Linuxforen, renomierten Blogs und Shops durchsucht wird.

-jonny- mag das.
Devil’s Pie
Zum Beispiel kann man eine Regel erstellen, sodass jedes Fenster mit Firefox im Titel an eine bestimmte Position verschoben wird, oder eine bestimmte Größe zugewiesen bekommt. Es ist auch möglich, Fenster auf andere Arbeitsflächen zu verschieben, sie zu maximieren, immer im Vordergrund anzuzeigen, oder nicht mehr in der Taskleiste anzuzeigen.
https://de.wikipedia.org/wiki/Devil%E2%80%99s_Pie
https://www.nongnu.org/devilspie2/
Rolling Release? Debian | Debian Testing
01:44 Debian Stable (Bullseye) installieren
07:24 Debian Stable 'rollend' machen
12:45 Es rollt
https://www.youtube.com/watch?v=lc-MuiH523A

Rolling Release? Debian | Debian Testing
01:44 Debian Stable (Bullseye) installieren07:24 Debian Stable 'rollend' machen12:45 Es rolltYouTube
How Google got to rolling Linux releases for Desktops
At Google we run large production fleets that serve Google products like YouTube and Gmail. To support all our employees, including engineers, we also run a sizable corporate fleet with hundreds of thousands of devices across multiple platforms, models, and locations. To let each Googler work in the environment they are most productive in, we operate many OS-platforms including a Linux system. For a long time, our internal facing Linux distribution, Goobuntu, was based off of Ubuntu LTS releases. In 2018 we completed a move to a rolling release model based on Debian.
Task vs. Process in Linux
In Linux programming and design, the terms “task” and “process” are sometimes used interchangeably. Learn more about them and how they differ.
https://blog.purestorage.com/purely-informational/task-vs-process-in-linux/
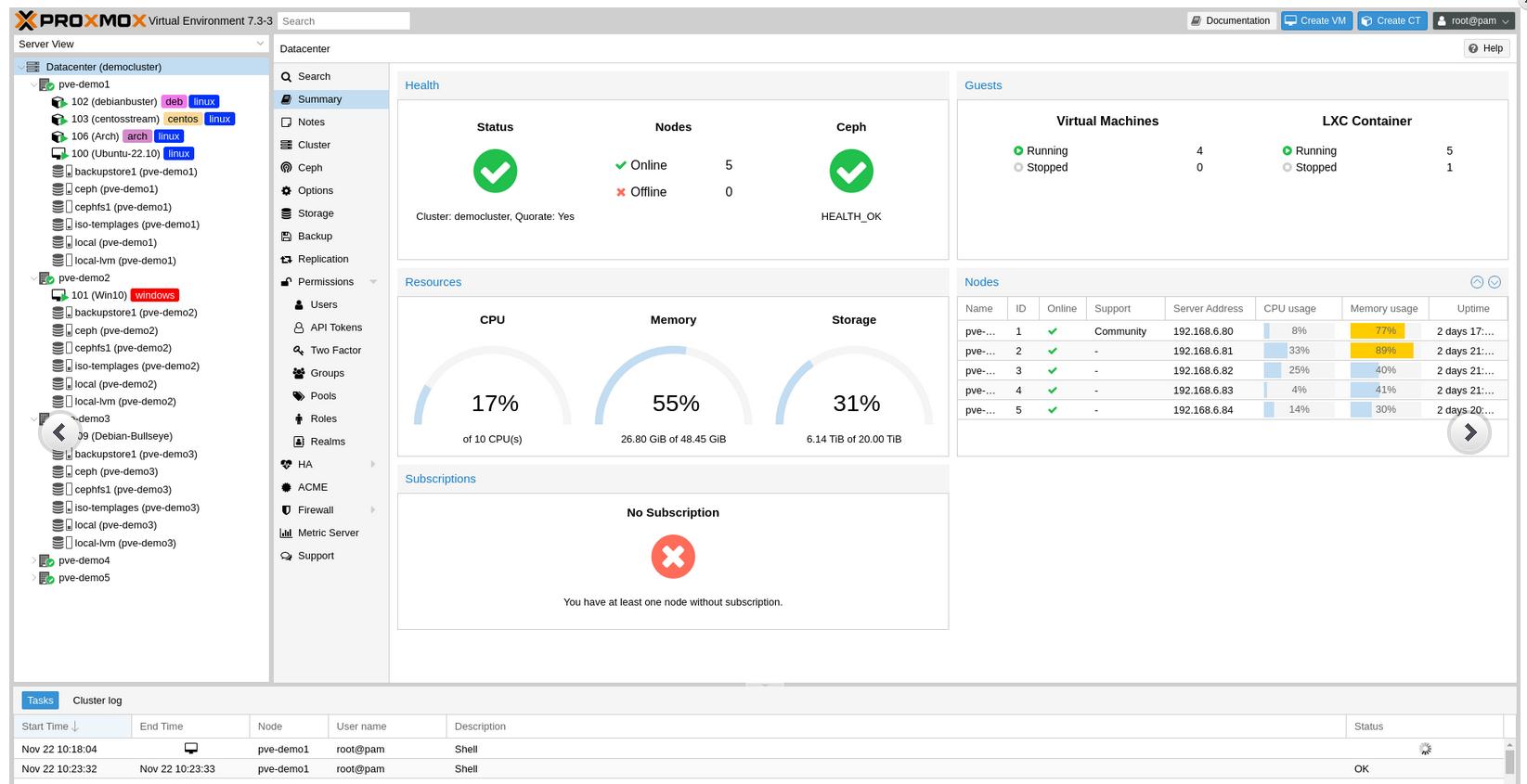
Proxmox Virtual Environment - Server, Netzwerk und Storage in einer Lösung
Proxmox VE ist eine komplette Open Source-Virtualisierungsplattform für Server. Es kombiniert KVM- und Container-basierte Virtualisierung und verwaltet virtuelle Maschinen, Container, Storage, virtuelle Netzwerke und Hochverfügbarkeits-Cluster übersichtlich über die zentrale Managementoberfläche.
Mit den vielen professionellen Funktionen und der intuitiven, web-basierten Verwaltungsoberfläche lassen sich vorhandene Ressourcen optimal ausschöpfen und nebenbei Hardware- und Administrationskosten, egal ob im Unternehmen oder privat, reduzieren. Mit Proxmox VE lassen sich problemlos die anspruchsvollsten Linux- oder Windows-Workloads virtualisieren.
Convert Plain English To Commands Using GPT-3 Powered Shell Genie
Shell Genie is a new command line tool that can be used to ask in plain English how to perform various tasks, and it gives you the shell command you need. To generate the commands, it uses OpenAI's GPT-3 or Free Genie, a free to use backend provided by the Shell Genie developer.
https://www.linuxuprising.com/2023/02/convert-plain-english-to-commands-using.html

Convert Plain English To Commands Using GPT-3 Powered Shell Genie
Shell Genie is a command line tool you can use to ask in plain English how to perform various tasks, and it gives you the command you need with GPT-3Linux Uprising Blog
How To Run A Command After The Previous One Has Finished On Linux
This article explains how to run a command after the previous command has finished running. Using this, you can run not just 2 commands, but any number of commands, after the previous one has finished. This will work with Sh, Bash, Zsh and other shells.
https://www.linuxuprising.com/2021/11/how-to-run-command-after-previous-one.html

How To Run A Command After The Previous One Has Finished On Linux
You can run a command after the previous one has finished running, depending on the previous command's exit status or regardless of this.Linux Uprising Blog
Running Synology Diskstation in an Alpine Linux chroot container
I have a Synology Diskstation DS115j. This NAS device has very limited resources, from today’s perspective:
256 MB RAM
CPU Marvell Armada-370 @800Mhz
USB 2.0 only
However, it is a neat little device which consumes not too much power.
Diese ver$%&§ Feststelltaste
Wer lange Texte am Computer schreibt, tippt häufiger mal versehendlich auf die Feststelltaste (englisch Caps Lock). Dabei ist es ganz einfach, dem nervenden Knöpfchen den Garaus zu machen.
https://www.linux-community.de/blog/diese-ver-feststelltaste/
Snapshots mit Timeshift erstellen
Zeitsprung
Ferdinand Thommes
Mit dem für Linux Mint entwickelten Tool Timeshift erstellen Sie einfach System-Snapshots, verwalten sie und spielen sie bei Bedarf wieder zurück.
Die Datensicherung betrachten bekanntermaßen viele Anwender als notwendiges, aber recht lästiges Übel. Idealerweise gestaltet man das Backup also so, dass man sich nur einmal Gedanken darüber machen muss: beim Erarbeiten einer Strategie, bei der die Software der Wahl künftig ohne weiteres Zutun diesen Job übernimmt.
https://www.linux-community.de/ausgaben/linuxuser/2019/06/zeitsprung/

Snapshots mit Timeshift erstellen - LinuxCommunity
Mit dem für Linux Mint entwickelten Tool Timeshift erstellen Sie einfach System-Snapshots, verwalten sie und spielen sie bei Bedarf wieder zurück. Die Datensicherung betrachten bekanntermaßen viele Anwender als notwendiges, aber recht lästiges Übel.Computec Media GmbH
Mit ImageMagick skriptgesteuert zeichnen
Silhouette
https://www.linux-community.de/ausgaben/linuxuser/2022/08/mit-imagemagick-skriptgesteuert-zeichnen/

Mit ImageMagick skriptgesteuert zeichnen - LinuxCommunity
ImageMagick kann mehr, als nur fertige Bilder zu bearbeiten. Die freie Software erstellt sogar automatisiert und skriptgesteuert einfache Zeichnungen.Computec Media GmbH
Healthchecks
Healthchecks is a cron job monitoring service. It listens for HTTP requests and email messages ("pings") from your cron jobs and scheduled tasks ("checks"). When a ping does not arrive on time, Healthchecks sends out alerts.
Healthchecks comes with a web dashboard, API, 25+ integrations for delivering notifications, monthly email reports, WebAuthn 2FA support, team management features: projects, team members, read-only access.
https://github.com/healthchecks/healthchecks

GitHub - healthchecks/healthchecks: A cron monitoring tool written in Python & Django
A cron monitoring tool written in Python & Django. Contribute to healthchecks/healthchecks development by creating an account on GitHub.GitHub
Write-up zu Firejail
Nach den Entwicklern ist Firejail ist eine SUID-Sicherheitssandbox, die auf Linux-Namespaces und seccomp-bpf basiert Es ist nichts einzigartiges an Firejail, da es im Wesentlichen einige Kernel-Sicherheitstechnologien verwendet, die übereinander geschachtelt sind. Der Vorteil ist damit, dass Komplexität für den Benutzer reduziert wird. Ausserdem bieten sie vorkonfigurierte Sicherheitsprofile für viele Programme an.
https://elsensohn.ch/docs/informationsecurity/firejail/
Write-up zu Firejail
Die Funktionsweise von Firejail wird mit ausführlichen Beispielen gezeigt.elsensohn.ch
User:Sakaki/Sakaki's EFI Install Guide/Sandboxing the Firefox Browser with Firejail
What is the most vulnerable application on your desktop? For most users, it is the web browser, since — in the picturesque phrase of Nick Congleton — it is "a large and complex piece of software with the ability to execute code, and it accesses the open Internet and executes just about everything that it comes into contact with".[1] Whilst selective-execution plug-ins such as NoScript can (and should[2][3][4]) be used to mitigate this risk, they cannot entirely remove it.
FSArchiver - Filesystem Archiver for Linux
FSArchiver is a system tool that allows you to save the contents of a file-system to a compressed archive file. The file-system can be restored on a partition which has a different size and it can be restored on a different file-system. Unlike tar/dar, FSArchiver also creates the file-system when it extracts the data to partitions. Everything is checksummed in the archive in order to protect the data. If the archive is corrupt, you just loose the current file, not the whole archive. Fsarchiver is released under the GPL-v2 license.
mögen das
Mehr Datensicherheit unter Linux dank ZFS und BTRFS

Mehr Datensicherheit unter Linux dank ZFS und BTRFS - NerdZoom.de
Wir erwarten von Datenträgern und Dateisystemen, dass diese unsere Daten sicher speichern. In der Praxis kommt es allerdings immer wieder zu unerwarteten und unentdeckten Datenverlusten. Wie kommt...Simon Raffeiner (NerdZoom.de)
Azure Cerulean mag das.
BTRFS Install (Kali Unkaputtbar)
BTRFS Install (Kali Unkaputtbar) | Kali Linux Documentation
Have you ever wished you could travel back in time after deleting that all important customer report or installing a broken driver just before heading into the board meeting? Well, you better read on, because now you can! All it takes is to install K…Kali Linux
Azure Cerulean mag das.
Raspberry Pi mit Ubuntu 20.04 LTS, Btrfs und Luks Verschlüsselung des Root Dateisystems + Remote Login
![Raspberry Pi mit Ubuntu 20.04 LTS, Btrfs und Luks Verschlüsselung des Root Dateisystems + Remote Login [Kommentar] - Torsten's Bücherecke](https://friendica.ambag.es/photo/preview/640/312248)
Raspberry Pi mit Ubuntu 20.04 LTS, Btrfs und Luks Verschlüsselung des Root Dateisystems + Remote Login [Kommentar] - Torsten's Bücherecke
Raspberry Pi mit Ubuntu 20.04 LTS und Luks Verschlüssung des Root Verzeichnisses mit Nutzung von BTRFS als Dateisystem + Remote EntsperrungTorsten (Torsten‘s Bücherecke)
Konvertieren von physischen Windows Systemen in virtuelle Maschinen damit sie auf einem Linux Desktop ausgeführt werden können
(funktioniert auch für Win 8+10, sowie später unter VirtualBox)

Konvertieren von physischen Windows Systemen in virtuelle Maschinen damit sie auf einem Linux Desktop ausgeführt werden können
Diese Anleitung veranschaulicht, wie man ein physisches Windows System (XP, 2003, 2000, NT4 SP4+) mit dem kostenlosen VMware Converter Starter in eine VMware virtuelle Maschine umwandeln kann.falko (HowtoForge)
Aktion Freiheit statt Angst mag das.
Den Unterschied zwischen sudo und su verstehen

Den Unterschied zwischen sudo und su verstehen
In diesem Artikel werden wir das "su"-Kommando im Detail besprechen und auch, wie es sich vom "sudo"-Kommando unterscheidet.howtoforge (HowtoForge)
N. E. Felibata 👽 mag das.
teilten dies erneut
Linux-Malware Shikitega tarnt Infektion
https://www.linux-magazin.de/ausgaben/2022/12/insecurity-bulletin/
Timeshift
Timeshift for Linux is an application that provides functionality similar to the System Restore feature in Windows and the Time Machine tool in Mac OS. Timeshift protects your system by taking incremental snapshots of the file system at regular intervals. These snapshots can be restored at a later date to undo all changes to the system
https://github.com/teejee2008/timeshift

GitHub - teejee2008/timeshift: System restore tool for Linux. Creates filesystem snapshots using rsync+hardlinks, or BTRFS snapshots. Supports scheduled snapshots, multiple backup levels, and exclude filters. Snapshots can be restored while system is runn
System restore tool for Linux. Creates filesystem snapshots using rsync+hardlinks, or BTRFS snapshots. Supports scheduled snapshots, multiple backup levels, and exclude filters. Snapshots can be re...GitHub
mögen das
Any feature requests, pull requests, or issues should be submitted to the Linux Mint repository.
https://github.com/linuxmint/timeshift
rsync-sidekick
What does this do?
rsync-sidekick propagates following changes (or any combination) from source directory to destination directory:
Change in file modification timestamp
Rename of file/directory
Moving a file from one directory to another
https://github.com/m-manu/rsync-sidekick

GitHub - m-manu/rsync-sidekick: Propagate file renames, movements and timestamp changes before rsync runs
Propagate file renames, movements and timestamp changes before rsync runs - GitHub - m-manu/rsync-sidekick: Propagate file renames, movements and timestamp changes before rsync runsGitHub
How to Pass Password to SCP Command in Linux using SSHPass
SCP stands for secure copy and is used to securely copy files or directories from one Linux environment to another.
Using the SCP command you can copy files or directories from a remote environment to a local environment, from a local environment to a remote environment, or between two remote environments in your local environment.
There are a number of benefits to using the SCP command to copy files i.e. you can limit the bandwidth which the channel can occupy using the -l tag.
SCP command supports password encryption to protect the data from leaking or files being snooped during transfer. Password encryption is what makes SCP secure.
https://bytexd.com/how-to-pass-password-to-scp-command-in-linux-using-sshpass/
How To Install and Run Android Apps on Ubuntu using Anbox
Have you ever thought of running Android applications on your Linux system? Well, that’s what we will show you in this article.
If you have used the Windows operating system or macOS, you must have encountered Bluestacks or Nox, which allows you to run Android applications on your PC.
Unfortunately, they don’t have any releases for Linux platforms – that’s where Anbox comes into play.
https://bytexd.com/how-to-install-and-run-android-apps-on-ubuntu-using-anbox/
Proxyjump, the SSH option you probably never heard of
Today, it is becoming more and more common for Penetration Testers, Security Researchers, Red Teams, and the like to require some sort of tunneling in and out of an organization’s infrastructure. Internal Red Teams, especially, who may need to cordon off their Command and Control Infrastructure will likely employ SSH (or VPN, but that will be a different post) tunnels from their External Infrastructure (such as callback servers, web hosting, mail, etc) to the Internal assets. Setting up these tunnels can become quite convoluted and difficult to manage, especially once the number of hops or jumps between servers increase.
https://medium.com/maverislabs/proxyjump-the-ssh-option-you-probably-never-heard-of-2d7e41d43464

Proxyjump, the SSH option you probably never heard of
Today, it is becoming more and more common for Penetration Testers, Security Researchers, Red Teams, and the like to require some sort of tunneling in and out of an organization’s infrastructure…Khris Tolbert (Maveris Labs)
Pi-hole failover using Gravity Sync and Keepalived
Traditionally when we assign DNS servers to hosts we assign more than one. For example, we may assign 8.8.8.8 as a primary an 8.8.4.4 as a secondary so in the unlikely event that one is ever down, we have a second one to fall back on. When we set up a single Pi-hole server with no failover we lose this redundancy, meaning that if our Pi-hole ever goes down or we want to restart it for updates, we lose DNS until it is back.
The simplest way to regain this redundancy is just to run 2 independent Pi-hole servers and set them as the primary and fallback DNS servers. However, this approach has a couple of disadvantages. The main problem is that we have no setting synchronisation between our servers. If we update the block lists on one, we have to remember to update them on the other. We also can’t guarantee which server clients will connect to, so if one is down, clients may still try to connect and then have to wait for a timeout before querying the second server. This can cause performance drops when one of the servers is offline.
https://davidshomelab.com/pi-hole-failover-with-keepalived/

Pi-hole failover using Gravity Sync and Keepalived - David's Homelab
Use Gravity Sync and IP failover to build a highly available Pi-hole cluster to keep your network online even if a single Pi-hole node fails.David (David's Homelab)
Azure Cerulean mag das.
Why did Debian Linux replace Google with DuckDuckGo?

Why did Debian Linux replace Google with DuckDuckGo? - LinuxLinks
Debian decided to feature DuckDuckGo, a more privacy-focused search engine, as their default oneLee Walker (LinuxLinks)
Remote reboots with encrypted disks
I've been using LUKS for full disk encryption on all my computers for many years. The main benefit is that if someone steals my computer, they don't get access to any of my personal data (unless they are very smart or have a $5 wrench). The main downside is that every time I reboot my computer, I have to type in the disk encryption password so it can actually boot.
https://tavianator.com/2022/remote_reboots.html#remote-reboots-with-encrypted-disks
CrowdSec on Linux or FreeBSD
CrowdSec is an open-source and lightweight software that allows you to detect peers with malevolent behaviors and block them from accessing your systems at various level (infrastructural, system, applicative).
To achieve this, CrowdSec reads logs from different sources (files, streams ...) to parse, normalize and enrich them before matching them to threats patterns called scenarios.
CrowdSec is a modular and plug-able framework, it ships a large variety of well known popular scenarios; users can choose what scenarios they want to be protected from as well as easily adding new custom ones to better fit their environment.
Detected malevolent peers can then be prevented from accessing your resources by deploying bouncers at various levels (applicative, system, infrastructural) of your stack.
One of the advantages of Crowdsec when compared to other solutions is its crowd-sourced aspect : Meta information about detected attacks (source IP, time and triggered scenario) are sent to a central API and then shared amongst all users.
Thanks to this, besides detecting and stopping attacks in real time based on your logs, it allows you to preemptively block known bad actors from accessing your information system.
Alpine Linux auf dem Raspberry Pi 3 installieren
Auch ein Alpine Linux lässt sich problemlos auf einem Raspberry Pi installieren. Warum jetzt Alpine und kein Raspberry Pi OS soll hier nicht das Thema sein!
https://www.bachmann-lan.de/alpine-linux-auf-dem-raspberry-pi-4-installieren/





tom s
Als Antwort auf tom s • •Wenn eine neue Stable-Version ansteht, wird testing eingefroren, bekommt in dieser Zeit dann nur Sicherheits-Updates.